arp病毒主机查找工具
- 大小:
- 下载:0
- 分类:软件下载
- 发布者:zhangliang
资源介绍
NBTSCAN能够得到PC的真正IP地址和MAC地址,如果有”ARP攻击”在做怪,能够寻找配有ARP攻击的PC的IP/和MAC地址。
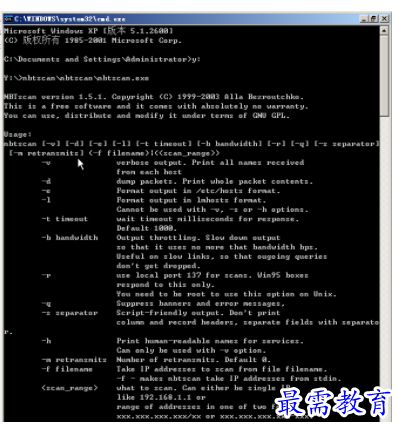
使用方法
nbtscan [-v] [-d] [-e] [-l] [-t timeout] [-b bandwidth] [-r] [-q] [-s separator]
[-m retransmits] (-f filename)|()
-v verbose output. Print all names received
from each host
-d dump packets. Print whole packet contents.
-e Format output in /etc/hosts format.
-l Format output in lmhosts format.
Cannot be used with -v, -s or -h options.
-t timeout wait timeout milliseconds for response.
Default 1000.
-b bandwidth Output throttling. Slow down output
so that it uses no more that bandwidth bps.
Useful on slow links, so that ougoing queries
don't get dropped.
-r use local port 137 for scans. Win95 boxes
respond to this only.
You need to be root to use this option on Unix.
-q Suppress banners and error messages,
-s separator Script-friendly output. Don't print
column and record headers, separate fields with separato
r.
-h Print human-readable names for services.
Can only be used with -v option.
-m retransmits Number of retransmits. Default 0.
-f filename Take IP addresses to scan from file filename.
-f - makes nbtscan take IP addresses from stdin.
what to scan. Can either be single IP
like 192.168.1.1 or
range of addresses in one of two forms:
xxx.xxx.xxx.xxx/xx or xxx.xxx.xxx.xxx-xxx.
NBTSCAN的应用案例:
假定搜索一台MAC地址为“000d870d585f”的病毒感染服务器。
1)将压缩文件中的nbtscan.exe 和cygwin1.dll压缩包解压放进c:下。
2)在Windows逐渐—运作—开启,输入cmd(windows98输入“command”),在发生的DOS窗口中输入:C: btscan -r 192.168.16.1/24(这儿必须结合客户具体子网输入),回车键。
3)根据查看IP--MAC相匹配表,查出来“000d870d585f”的病毒感染服务器的IP地址为“192.168.16.223”。